Orange Pi Plus Setup, Benchmarks, and Initial Impressions
tl;dr: The Orange Pi Plus offers much better specs, and much better performance, than a similarly-priced Raspberry Pi. Unfortunately—and this is the case with most RPi competitors at this time—setup, hardware support, and the smaller repository of documentation and community knowledge narrow this board's appeal to enthusiasts willing to debug annoying setup and configuration issues on their own.
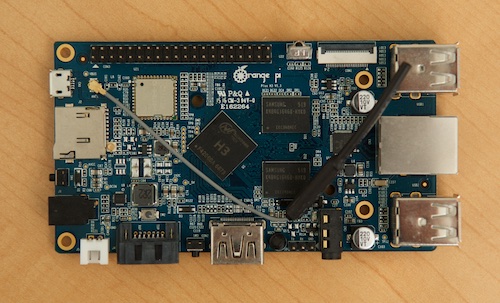
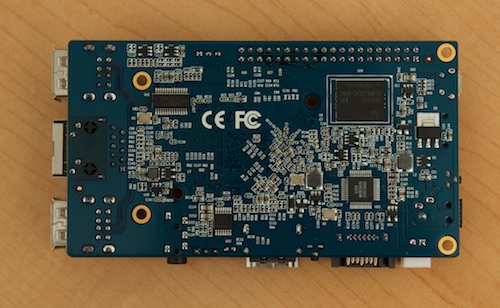
A few months ago, I bought an Orange Pi Plus from AliExpress. It's a single-board Linux computer very similar to the Raspberry Pi, with a few key differences: